How to Spot Apple ID Phishing Scams
Apple is known for its nearly impenetrable security. But no system is fail-safe. Even Apple devices and users sometimes become victims of hackers and iPhones can get viruses. One of the most common ways is through a scam known as Apple ID phishing. In fact, phishing accounted for about a third of all data breaches in 2019, and 10 percent involved attempts to steal someone’s Apple ID or password. Consider these 18 secrets from people who never get hacked.
What is an Apple ID phishing scam?
Phishing, a type of smishing, is a scheme in which hackers try to trick you into divulging personal information, such as passwords and Social Security numbers. They accomplish this by sending emails, texts, and other types of messages that look like they’re coming from a legitimate company, like Amazon, your bank, or your email provider. These messages typically have a link that, when clicked, takes you to a spoofed website, where your data may be stolen. Look out for these nine red flags that you’re about to fall for a phishing email and learn how to block emails like this for good.
In an Apple ID phishing scam, hackers are specifically trying to get you to give up your Apple ID and password. Apple requires user IDs and passwords to access Apple services like the App Store, Apple Music, iCloud, iMessage, and FaceTime. Says Russel Kent-Payne, director and co-founder of Certo Software, “If configured correctly, iPhones can be quite secure, so sometimes phishing is the only option for hackers.”
Why would someone phish for your Apple ID?
Your Apple ID account contains all your contact, payment, and security information. If hackers discern your ID and password, they can dig even deeper, gaining private information either for their own nefarious uses or to sell on the black market. “The bad guys get access to your iCloud email, and the history of your app, music, and movie purchases and rentals,” says Chris Hauk, consumer privacy champion at Pixel Privacy. They also have entrée to all your documents, photos, and files stored on your iCloud drive. They can even use your account to watch your movies.
In fact, in 2019, individuals and businesses lost more than $3.5 billion in online scams, and phishing was the most common method, according to the FBI’s Internet Crime Complaint Center (IC3). Find out the things hackers can do with just your phone number.
How do Apple ID scams work?
Scammers have become very savvy and will use any method available to them to get your attention and try to phish for your information. Hauk says spoofed emails and texts are the most common methods. “They’re the easiest to pull off and don’t require any real programming skills on the part of the bad actor.”
But scammers will also target you through browser pop-up notices, phone calls, and even calendar invitations. Usually, they try to entice you to click on a link or call a phone number for legitimate-sounding purposes but are actually trying to either steal or get you to divulge personal information. Often, scammers create a sense of urgency, says Kent-Payne, “so that their victims react quickly to the message and are then less likely to spot that it’s a fake.” They may even create a fake Apple virus warning.
What are the main Apple ID phishing scams to be aware of?
Hackers are continually inventing new scams but some of the most enduring ones include the following:
Apple ID order receipt: In this type of scam, you’ll receive an email that appears to be from Apple, stating that your ID has been used to make a purchase, usually with a PDF receipt attached as “proof.” The email will either ask you to confirm the purchase or submit payment for it. In either instance, there are typically links that, if clicked, will take you to a fake Apple account management page. “It attempts to entice you to give up your Apple ID and password,” Hauk says.
Apple ID locked. This scam often works in tandem with the fake receipt scam. If you do follow a spoofed email to a fake Apple page, and then input your information, you may see a notification telling you that your account has been locked due to suspicious activity. Then, it will show you an “unlock” button, which requires you to divulge personally identifying information, such as your name, Social Security number, payment information, and answers to common security questions. Sometimes, this scam will arrive via an iMessage alert stating that your Apple ID has been locked because your ID is about to expire. The message might ask you to complete a form to unlock your account, which of course gives the hackers access to sensitive info. It’s true that Apple IDs sometimes are locked if Apple suspects fraudulent activity, but they can be unlocked with a phone call that you place directly to Apple. However, Apple IDs don’t expire, Kent-Payne says.
Apple support scam: In this scam, you usually receive a phone call—or often, several calls in less than an hour— from what appears to be the real Apple support phone number, but instead the number has been spoofed. If you answer the call, the scammer claims to be from Apple and says your account or Apple ID has been compromised; to fix things for you, they’ll say, they need your password or other sensitive information. Sometimes, rather than speaking with you directly, scammers will leave an automated voice message directing you to call a specific number for “Apple support.” If you call the number, everything sounds legitimate, including updates telling you the anticipated hold time. When you finally connect with a human, they will ask you for compromising information. For the record, Apple will never call you to notify you of suspicious activity. In fact, Apple won’t call you for any reason—unless you request a call first. Phone scams like these are also known as vishing.
iPhone locked: If you get hit with this scam, you’ve probably already fallen for at least one other Apple ID scam. If hackers have already gained access to your iCloud account, they could activate the “Find My iPhone” feature and place your device into “lost” mode, which remotely locks it. Then you’ll see a pop-up message on your phone saying that it will remain locked until you pay a ransom.
Calendar invitation: You might receive a spammy iCloud calendar invitation to a meeting or event from an unknown individual or group, often with promises for easy money, pornography, or pharmaceuticals. You guessed it: If you click on a link or respond to the invitation in any way, you’re opening yourself up to phishing or, at the very least, more spam. Here’s how to stop iPhone calendar spam.
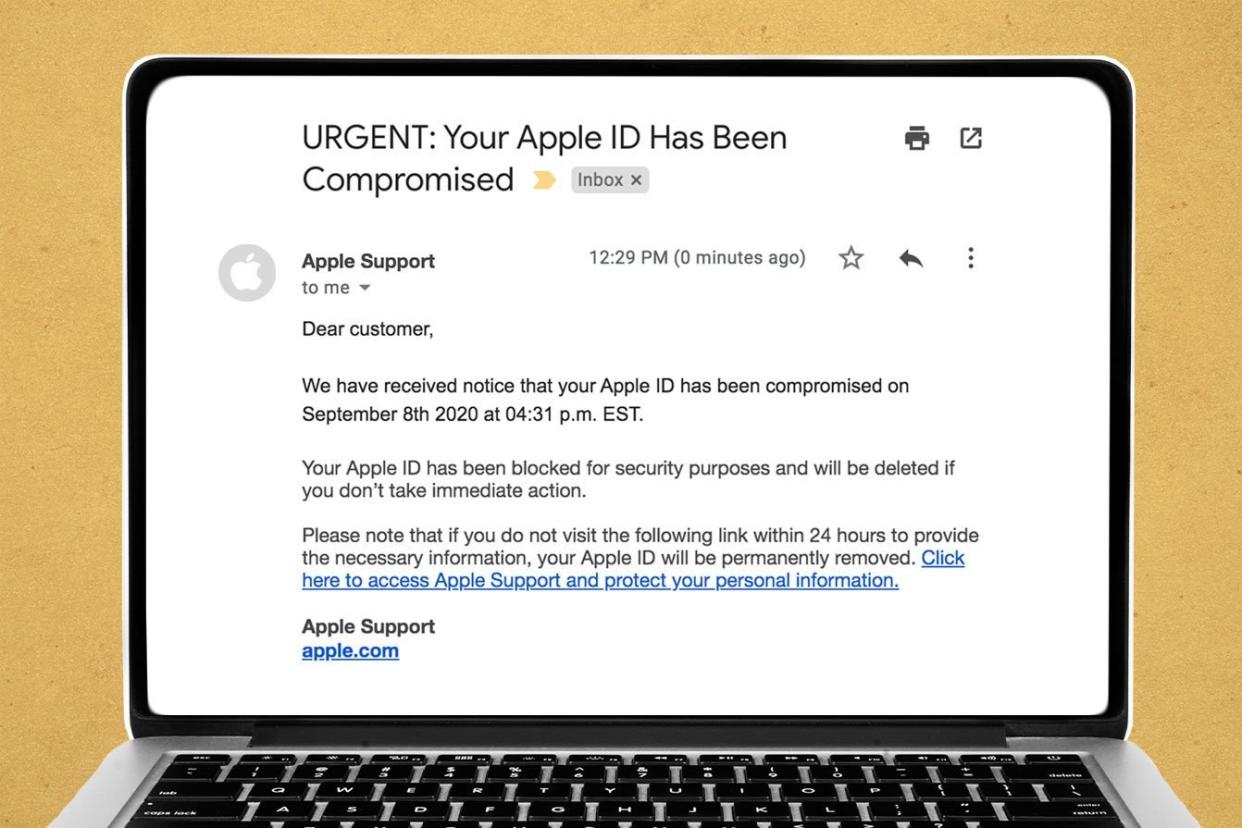
How to spot Apple ID phishing scams
Scammers are becoming increasingly sophisticated in the art of making emails, texts, and other communications look like the real deal. “Being able to recognize an attack is key to protecting yourself against phishing,” says Kent-Payne. Here’s what to look for.
Spoofed address. Hover on the sender’s name in your inbox to see the full email address. If the message claims to be from Apple but the address is off by a letter or two—or worse, is just a bunch of random letters and numbers—it’s probably a phishing attempt.
Vague greeting. Reputable companies will usually address you by your full name, says Kent-Payne. Scammers will use something more generic, like “dear friend.”
Misspellings, grammar mistakes, and obvious typos. Reputable companies take pains to make sure their communication is clear, accurate, and precise.
A sense of urgency. Phishing scams often create a false sense of urgency or rely on emotional manipulation to get you to act quickly.
Any legitimate email related to your Apple ID account will always come from appleid@id.apple.com. In addition, emails from Apple will never ask you to disclose your Apple ID password, Social Security number, your mother’s maiden name, your full credit card number, or your credit or debit card’s CCV security code.
In addition, Apple says, “Genuine purchase receipts—from purchases in the App Store, iTunes Store, iBooks Store, or Apple Music—include your current billing address, which scammers are unlikely to have.” You can also check your purchase history from any device without clicking on links in suspicious emails.
How to protect yourself from Apple ID phishing scams
The best way to avoid becoming the victim of a phishing attack is to never click on a link or attachment within an email, text message, or pop-up unless you’re 100 percent certain the message is real.
The same holds true for phone calls. Apple and other companies will never call you out of the blue to discuss your device’s security. Don’t accept these calls or click on hyperlinked phone numbers within messages—and never answer a call from one of the suspicious area codes. If you have a concern about your device, call Apple’s support number directly at 1-800-275-2273.
In addition to ignoring unsolicited communication, Kent-Payne suggests enabling two-factor authentication for any important accounts, including Apple ID, email, social media, and banking. “This means that even if a hacker works out your password via a phishing attack, they still can’t access your account,” he says.
He also recommends using Apple’s Message Filtering. That feature separates out any texts you receive from people who are not in your contacts and sends them to the “unknown senders” tab in your Messages list. You can turn on message filtering in Settings. If you use filtering in conjunction with a good security app, such as Truecaller or SpamHound, the app can alert you when you receive a phishing message, Kent-Payne says.
Also, be sure to adhere to the following best practices:
Never share your Apple ID password with anyone, including someone who says they’re from Apple.
Keep your operating system updated to the latest version.
Keep your browsers updated. Also consider using a browser like Chrome, which has built-in phishing protections.
Use antivirus and anti-malware programs on your devices.
Always check the URL of any website where you’re entering sensitive information. It should always start with “https” (the “s” stands for “secure”).
Don’t reuse the same password on multiple sites. That just makes it easier for hackers.
What should you do if you receive an Apple ID phishing attempt?
In most cases, you can safely close and ignore the email, text, or pop-up, or hang up on the caller. Whatever you do, don’t click on any links or provide any personal information to the scammer. You should, however, report the attempt to the appropriate parties.
If you receive a fraudulent email, you should forward it to reportphishing@apple.com. If you receive a suspicious iMessage or calendar invite, you should have an option under the message to “Report Junk.” If the option doesn’t appear, you can still block the sender. And if you get a fake tech-support phone call, you can report it to your local police department and to the Federal Trade Commission.
And if you do happen to accidentally click on a suspicious link, don’t panic. “As long as you don’t supply any information that might be requested on a linked webpage, you should be OK,” Hauk says. If you did enter personal information, you should immediately change your Apple ID password and enable two-factor authentication. Then review all the security information in your account to make sure it’s still accurate. This can include your name, your primary Apple ID email address and any other rescue emails or phone numbers, and your security questions and answers. You should also check to see where your Apple ID is being used. You can find that information by going to Settings, and then clicking on your name. If you see a device you don’t recognize, you can remove it from the list.
For more help on avoiding Apple ID phishing scams, check out the following resources from Apple:
Sources:
Russel Kent-Payne, director and co-founder of Certo Software
Chris Hauk, consumer privacy champion at Pixel Privacy
What Is Vishing?
What Is Smishing?
If You Get This Phone Call, You're About to Get Scammed
The post How to Spot Apple ID Phishing Scams appeared first on Reader's Digest.



